As people trend towards remote work, IT departments have an ongoing need to provide remote services to end users. Without the use of traditional VPNs, technologies like Remote Desktop, Citrix and VMware are commonly used for remote access. However, they are not always configured in secure ways.
During the height of the pandemic, we setup two servers with Remote Desktop exposed to the Internet and created user "hello" with no password. Obviously, this is not a smart idea, but it does demonstrate what can happen when you have unsecured assets that are available directly on the Internet.
Scenario 1: Network Scanner Resulting in Abuse Complaint
A scanning tool was used to scan for other servers listing on port 3389, which resulted in a complaint from Hetzner Online GmbH. The complaint was as follows:
 |
| Figure 1: Abuse Complaint Received |
It is good that Hetzner has automated monitoring systems that will send abuse complaints automatically and one step in the right direction to make the Internet a safer place.
Scenario 2: LockBit Ransomware
LockBit is a ransomware variant that reportedly emerged in 2019. It functions as a ransomware-as-a-service (RaaS) model where developers write the encryptors and then share out encryptors to affiliates who conduct intrusions and deploy the encryptor on victim systems. As victims pay the ransom, the developers get a percentage or commission based on the total ransom paid.
In this scenario, the first unauthorized logon originated from the IP address 82.102.20.219, however no malicious activity appeared to take place as a result of this login. Interestingly enough, three additional logons are observed from IP addresses afterwards, leading up to a final logon when LockBit ransomware is deployed. A timeline of events is below:
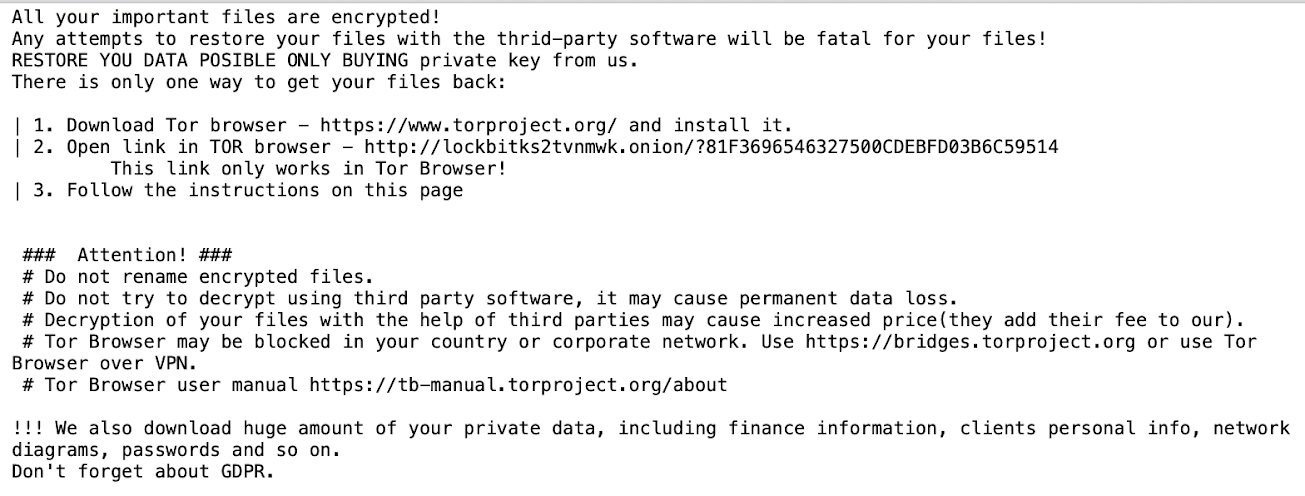
Once the ransomware executable is run on the system, it proceeds to delete Volume Shadow Copies as one of the steps to inhibit recovery efforts. As files are encrypted, a ransom note named Restore-My-Files.txt is dropped:
The threat actor then returns to the system an hour later to run screensaver.exe, which is a malware known as ScreenLocker that effectively locks your screen and prevents you from using the system.
We've captured the indicators into our database and made them searchable on sicehice.com. As an example, you can use our Bulksearch feature to download a CSV formatted list of lookups for these IPs.
Indicators of Compromise
| IOC | Type | Description |
| 54.38.212.197 | IPv4 | RDP Bruteforce IP |
| 185.202.2.121 | IPv4 | RDP Bruteforce IP |
| 51.89.134.150 | IPv4 | RDP Bruteforce IP |
| 104.237.255.254 | IPv4 | RDP Bruteforce IP |
| 62.76.112.121 | IPv4 | RDP Bruteforce IP |
| 167.172.239.68 | IPv4 | RDP Bruteforce IP |
| 82.202.247.81 | IPv4 | RDP Bruteforce IP |
| 82.102.20.219 | IPv4 | Unauthorized RDP Login |
| 51.15.18.180 | IPv4 | Unauthorized RDP Login |
| 52.237.96.13 | IPv4 | Unauthorized RDP Login |
| f9073cc6566ba11318b425a761f1ce17 | MD5 | ScreenLock Executable: screensaver.exe |
| 1f4581b36253f0f5d63e68347d1744a7 | MD5 | LockBit Executable: 81F3696546327500.exe |
| bfc879a4a959a3bd23892448afbd75b6 | MD5 | Ransom Note: Restore-My-Files.txt |

Comments
Post a Comment